You thought your IT security is watertight? Think again. Security issues or breaches are nearly impossible to avoid. Therefore, not only the technology you use is crucial, it’s the strategy you build around it that makes the difference: adequate awareness, prevention, and response in case of an issue. To prevent or minimise impact, Dilaco will identify risks and create a defence strategy to improve your security approach.
Our certified consultants advise and/or guide you in a professional and human way.
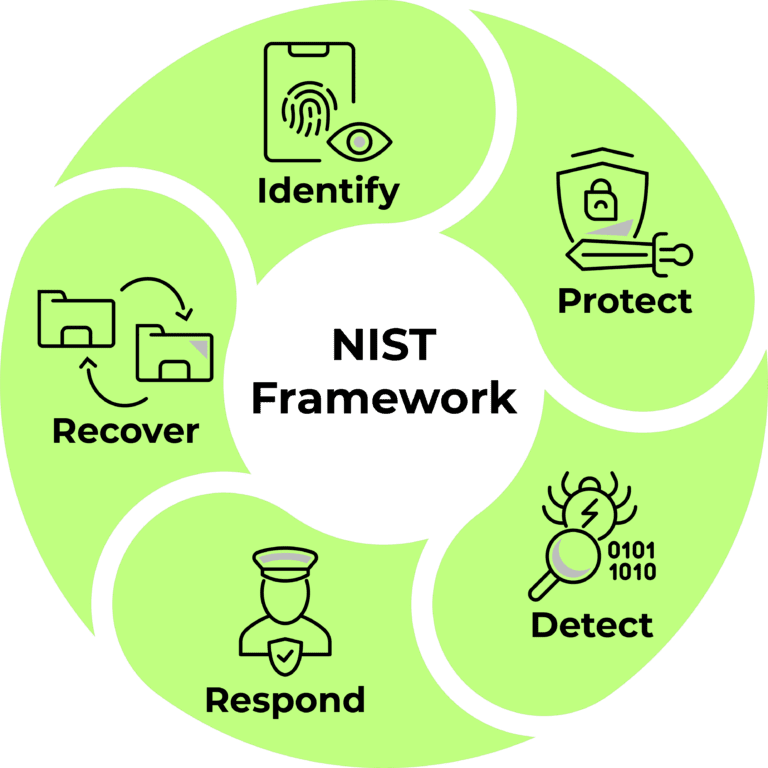
A full range of services and solutions for each stage of the NIST framework.
A secure yet optimal end-user experience is the key to every solution or action we propose.

A house will never be constructed without an architectural plan. The same goes for cybersecurity. A good program is the key to building a cyber resilient infrastructure. However, building a cyber security program is often neglected by many organisations due to the lack of time or knowledge.
We can help you get an overview of the risks that impact the information systems and data you rely upon to operate.
Data leaves your company in many ways, and even with the best firewalling solutions and end-user awareness trainings, you aren’t always aware of where your data is going. This makes your company data inherent insecure.
At Dilaco we believe in an approach where you follow and secure your data, constantly. You need to know which data exists in your company, you need to know when and where new data is created, and how it’s moving around.
We integrate our tooling seamlessly into Microsoft Azure, ensuring the protection of your data. How, you ask?


One of the biggest challenges for IT managers is protecting their organisation from cyber threats, without limiting the productivity of the people who work there. But the end-user will in a way always feel limited, and will use back doors to try and get done what they want. Enter shadow IT. Malware, data loss and compliancy violations are just around the corner now.
We can help you shine a light on these IT application in the shadow, while keeping the end-user performance intact.
The NIST framework is a guideline for companies who want to reduce their cyber security risks. Dilaco carefully selected technologies and developed solutions for every stage of the framework.
Through this framework, we can analyse which steps your company already covers and which are leaving holes in your cyber security.

We can map out your crown jewels and to which threats these are exposed.

We can help you select the right methods and tools to put on a strong protection.

The methods used in this pillar are dependent on the protection tooling used in pillar 2. We can advise you on the most effective ways to collect log files in a central place and make the right correlations in order to notice a breach.

We will define a (partly) automated strategy by linking actions to certain correlations and anomalies. The goal is to avert any and every possible danger, without leaving a trace or obstructing the end-user.
We're going to measure any damage, repair it, and define the lessons learned. The threats and vulnerabilities faced, will be added to pillar one, and so the circle is complete.
Identify
First, identify all your assets and threats. This pillar is the most crucial one, as it is the groundwork of your security plan.
We can map out your crown jewels and to which threats these are exposed.
Protect
During the protect phase, you should be outlining and implementing your protection strategy.
We can help you select the right methods and tools to put on a strong protection.
Detect
The two previous pillars make the chance of a breach smaller, but not non-existent. If a breach does occur, there is 1 golden rule: the faster you detect it, the smaller the damage.
The methods used in this pillar are dependent on the protection tooling used in pillar 2. We can advise you on the most effective ways to collect log files in a central place and make the right correlations in order to notice a breach.
Respond
In this pillar you define your response strategy, at least part of which will be automated.
We will define a (partly) automated strategy by linking actions to certain correlations and anomalies. The goal is to avert any and every possible danger, without leaving a trace or obstructing the end-user.
Recover
A step that’s often forgotten, but none the less invaluable. It will save time and money in the future.
We’re going to measure any demage, repair it, and define the lessons learned. The threats and vulnerabilities faced, will be added to pillar one, and so the circle is complete.







| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |